Our computer and related device services covers a wide range of working with data from computers, mobile phones, data loggers, modems, voice recorders, digital copiers, hard-drives and USB devices.
We provide full services from data image capture, data analysis, key logging analysis, IP address interrogation, send and receive confirmation, analysing suspect file manipulation and deletion recovery.
Computers
Forensics Australia has recovered, preserved and examined a broad range of computer devices for court or corporate matters. Compliance with expected high standards of forensic practice are maintained and examinations range from simple extractions through to complex crimes.
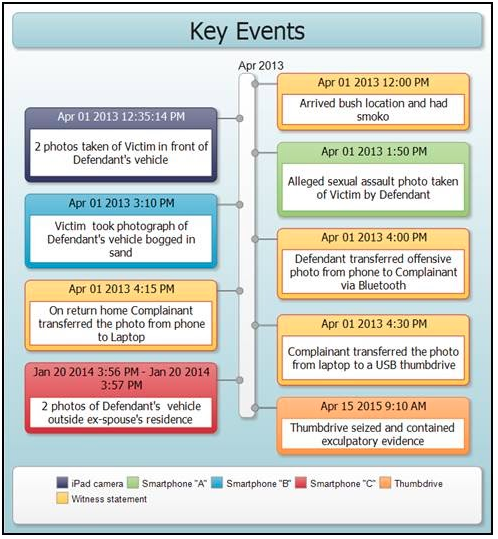
Our forensic reports are concise, easily navigable and understood for the lay person without any forensic background or training. Our reports provide event reconstruction and make use of timelines, relationship diagrams, charts, figures and links to key evidence artefacts, without over burdening the reader with a miasma of technical complexity.
We are often called upon to seek incriminating evidence and exculpatory evidence regarding candidate suspects. Whilst recovering and reviewing evidence we adopt an evidence-led and scientific approach to avoid the pitfalls of prejudicing our opinion by selecting what appears to be ‘obvious’ and denying full justice for those involved. We have been able to identify vexatious complaints that relied on a subjective view of evidence that was later shown to be false or at best unreliable.
Online Data Recovery
Some of the software applications that may be recovered from online servers include Microsoft Exchange, Apple, Facebook, Dropbox and Instagram. Access to these servers must be approved by the account holders or under a court order. In any event, the account holders’ assistance in providing passwords or account tokens must be obtained to gain access.
The process of downloading this information should be forensically sound as distinct from the users downloading the information themselves. It is prudent to access and recover this data as a matter of priority so as to preserve any evidence that may be present.
Mobile Phones & Hand-held Devices
Mobile devices are in effect mobile laptop and desktop computers attempt to hold a lot more personal information that might be found on laptops and desktop computers. There has been an exponential increase in the reliance on digital evidence in both criminal and civil legal proceedings. Mobile devices are becoming even more relied upon in these proceedings and the recovered evidence can often be the only evidence used.
In addition to a growing variety of smartphones and platforms, including Android, Blackberry, Apple iPhone, and Windows Mobile, there is a staggering range of inexpensive phones using legacy systems.
Data stored on mobile devise is frangible and can be easily lost, destroyed or altered thereby reducing its value. It should be retrieved and observed using appropriate forensic process and tools. Similarly, data stored online such as Facebook and Dropbox files, routinely made use of during trials, should be recovered promptly and forensically preserved for further examination.
Mobile phones and other handheld devices store personal information including:
- Call history;
- Internet browsing records;
- Online social interactions such as WhatsApp, KIK, etc;
- File downloads and uploads;
- Geographical locations;
- Text messages and chat histories;
- Emails;
- Multimedia files;
- Contact lists;
- Calendar events; and
- Deleted data, etc.
Stored information often reveals details of the user’s contacts and communications with other persons or websites and may provide an into the motivation and mindset and at times, the innocence of alleged transgressors.
We are able to reconstruct timelines or events and relationship diagrams from mobile phone and computer data to assist with event reconstruction and legal strategy development.